Jump to page sections
Having a need to install PFX certificates on various 2008 R2 servers with PowerShell version 2, I couldn't use the new 2012 R2/Win 8.1 (PSv4) Import-PfxCertificate cmdlet. Using the code I found here in "mao47"'s answer as a base, I wrote up some code to remotely install PFX certificates - supporting specific certificate stores.I copy to a temporary file in the remote \\computer\admin$ share and then use PowerShell remoting to run the code to import it remotely, so this requires that both administrative shares via SMB/CIFS and PSRemoting are configured and available in the environment.
Client operating systems starting from Vista(?), at least from Windows 7 on, do not by default expose the administrative shares, as far as I can remember from when I set up a GPO for Windows 7 clients and tested stuff. This can be enabled on clients via a GPO, but does represent a security risk. Servers should have them enabled by default unless it's overridden by a group policy (GPO) in your environment.By default it installs with the flags ''PersistKeySet'' and ''MachineKeySet''. The flags are documented here. Send them in in a string separated by commas.
The X509Certificates class I use under System.Security.Cryptography is documented here.This isn't a super polished product, but should be perfectly usable for various scenarios, and can be adapted as needed (editing the source code if the parameters aren't enough for you).
Example of successful import
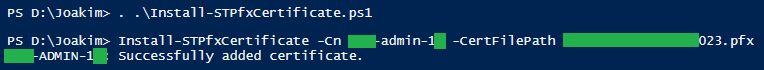
PS D:\> . .\scripts\Import-STPfxCertificate.ps1 PS D:\> Import-STPfxCertificate -Cn admin-01 -CertFilePath \\someserver\Cert\AD2023.pfx ADMIN-01: Successfully added certificate.
Parameters
| ComputerName | Target computer(s). (alias: -Cn) |
| CertFilePath | Path to the PFX certificate you want to install, as found in an accessible file system. |
| CertRootStore | Certificate root store to install to. Default: 'localmachine'. |
| CertStore | Certificate store within root store to install to. Default: 'my' ("Personal" when viewed in mmc.exe). |
| X509Flags | X509 flags to pass to the import method. Default: 'PersistKeySet,MachineKeySet'. Documented here. |
| Password | Leave empty to be prompted for the PFX certificate password. System.SecureString. You can store it beforehand with "$mypass = Read-Host -AsSecureString" |
Download
Earlier versions (if any):
Import-STPfxCertificate.ps1.txt.
Source code
#requires -version 2
function Import-STPfxCertificate
{
[CmdletBinding()]
param(
[Parameter(Mandatory=$true)][Alias('Cn')] [string[]] $ComputerName,
[Parameter(Mandatory=$true)][string] $CertFilePath,
[string] $CertRootStore = 'localmachine',
[string] $CertStore = 'My',
[string] $X509Flags = 'PersistKeySet,MachineKeySet',
[System.Security.SecureString] $Password = $null)
$ErrorActionPreference = 'Continue'
$TempCertFileName = 'Svendsen.Tech.temporary.abcdefg.pfx'
if ($Password -eq $null)
{
$Password = Read-Host -Prompt 'Enter PFX cert password' -AsSecureString
}
foreach ($Computer in $ComputerName)
{
$Destination = "\\$Computer\admin$\$TempCertFileName"
try
{
Copy-Item -LiteralPath $CertFilePath -Destination $Destination -ErrorAction Stop
}
catch
{
Write-Error -Message "${Computer}: Unable to copy '$CertFilePath' to '$Destination'. Aborting further processing of this computer."
continue
}
Invoke-Command -ComputerName $Computer -ScriptBlock {
param(
[string] $CertFileName,
[string] $CertRootStore,
[string] $CertStore,
[string] $X509Flags,
$PfxPass)
$CertPath = "$Env:SystemRoot\$CertFileName"
$Pfx = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2
# Flags to send in are documented here: https://msdn.microsoft.com/en-us/library/system.security.cryptography.x509certificates.x509keystorageflags%28v=vs.110%29.aspx
$Pfx.Import($CertPath, $PfxPass, $X509Flags) #"Exportable,PersistKeySet")
$Store = New-Object -TypeName System.Security.Cryptography.X509Certificates.X509Store -ArgumentList $CertStore, $CertRootStore
$Store.Open("MaxAllowed")
$Store.Add($Pfx)
if ($?)
{
"${Env:ComputerName}: Successfully added certificate."
}
else
{
"${Env:ComputerName}: Failed to add certificate! $($Error[0].ToString() -replace '[\r\n]+', ' ')"
}
$Store.Close()
Remove-Item -LiteralPath $CertPath
} -ArgumentList $TempCertFileName, $CertRootStore, $CertStore, $X509Flags, $Password
}
}
Powershell
Windows
Cryptography
Blog articles in alphabetical order
A
- A Look at the KLP AksjeNorden Index Mutual Fund
- A primitive hex version of the seq gnu utility, written in perl
- Accessing the Bing Search API v5 using PowerShell
- Accessing the Google Custom Search API using PowerShell
- Active directory password expiration notification
- Aksje-, fonds- og ETF-utbytterapportgenerator for Nordnet-transaksjonslogg
- Ascii art characters powershell script
- Automatically delete old IIS logs with PowerShell
C
- Calculate and enumerate subnets with PSipcalc
- Calculate the trend for financial products based on close rates
- Check for open TCP ports using PowerShell
- Check if an AD user exists with Get-ADUser
- Check when servers were last patched with Windows Update via COM or WSUS
- Compiling or packaging an executable from perl code on windows
- Convert between Windows and Unix epoch with Python and Perl
- Convert file encoding using linux and iconv
- Convert from most encodings to utf8 with powershell
- ConvertTo-Json for PowerShell version 2
- Create cryptographically secure and pseudorandom data with PowerShell
- Crypto is here - and it is not going away
- Crypto logo analysis ftw
D
G
- Get rid of Psychology in the Stock Markets
- Get Folder Size with PowerShell, Blazingly Fast
- Get Linux disk space report in PowerShell
- Get-Weather cmdlet for PowerShell, using the OpenWeatherMap API
- Get-wmiobject wrapper
- Getting computer information using powershell
- Getting computer models in a domain using Powershell
- Getting computer names from AD using Powershell
- Getting usernames from active directory with powershell
- Gnu seq on steroids with hex support and descending ranges
- Gullpriser hos Gullbanken mot spotprisen til gull
H
- Have PowerShell trigger an action when CPU or memory usage reaches certain values
- Historical view of the SnP 500 Index since 1927, when corona is rampant in mid-March 2020
- How Many Bitcoins (BTC) Are Lost
- How many people own 1 full BTC
- How to check perl module version
- How to list all AD computer object properties
- Hva det innebærer at særkravet for lån til sekundærbolig bortfaller
I
L
M
P
- Parse openssl certificate date output into .NET DateTime objects
- Parse PsLoggedOn.exe Output with PowerShell
- Parse schtasks.exe Output with PowerShell
- Perl on windows
- Port scan subnets with PSnmap for PowerShell
- PowerShell Relative Strength Index (RSI) Calculator
- PowerShell .NET regex to validate IPv6 address (RFC-compliant)
- PowerShell benchmarking module built around Measure-Command
- Powershell change the wmi timeout value
- PowerShell check if file exists
- Powershell check if folder exists
- PowerShell Cmdlet for Splitting an Array
- PowerShell Executables File System Locations
- PowerShell foreach loops and ForEach-Object
- PowerShell Get-MountPointData Cmdlet
- PowerShell Java Auto-Update Script
- Powershell multi-line comments
- Powershell prompt for password convert securestring to plain text
- Powershell psexec wrapper
- PowerShell regex to accurately match IPv4 address (0-255 only)
- Powershell regular expressions
- Powershell split operator
- Powershell vs perl at text processing
- PS2CMD - embed PowerShell code in a batch file
R
- Recursively Remove Empty Folders, using PowerShell
- Remote control mom via PowerShell and TeamViewer
- Remove empty elements from an array in PowerShell
- Remove first or last n characters from a string in PowerShell
- Rename unix utility - windows port
- Renaming files using PowerShell
- Running perl one-liners and scripts from powershell
S
- Sammenlign gullpriser og sølvpriser hos norske forhandlere av edelmetall
- Self-contained batch file with perl code
- Silver - The Underrated Investment
- Simple Morningstar Fund Report Script
- Sølv - den undervurderte investeringen
- Sort a list of computers by domain first and then name, using PowerShell
- Sort strings with numbers more humanely in PowerShell
- Sorting in ascending and descending order simultaneously in PowerShell
- Spar en slant med en optimalisert kredittkortportefølje
- Spre finansiell risiko på en skattesmart måte med flere Aksjesparekontoer
- SSH from PowerShell using the SSH.NET library
- SSH-Sessions Add-on with SCP SFTP Support
- Static Mutual Fund Portfolio the Last 2 Years Up 43 Percent
- STOXR - Currency Conversion Software - Open Exchange Rates API
